Guardians of the Digital Realm: Securing Malaysia's Future
As Malaysia accelerates its digital transformation, the stakes for cybersecurity have never been higher. The nation faces over 3,000 cyberattacks daily, compelling organisations to defend against sophisticated phishing scams and manage vulnerabilities within cloud environments. But it's not just about the tech – businesses here are also dealing with alert fatigue (think: non-stop security warnings) and a serious talent crunch when it comes to cybersecurity skills (Malaysia’s Cyber Security Academy, set up by CyberSecurity Malaysia, is expected to begin operations in the second quarter of 2025). These factors complicate the ability of security teams to keep pace and respond effectively to emerging threats.
Have something to contribute around cybersecurity in the Southeast Asia region?

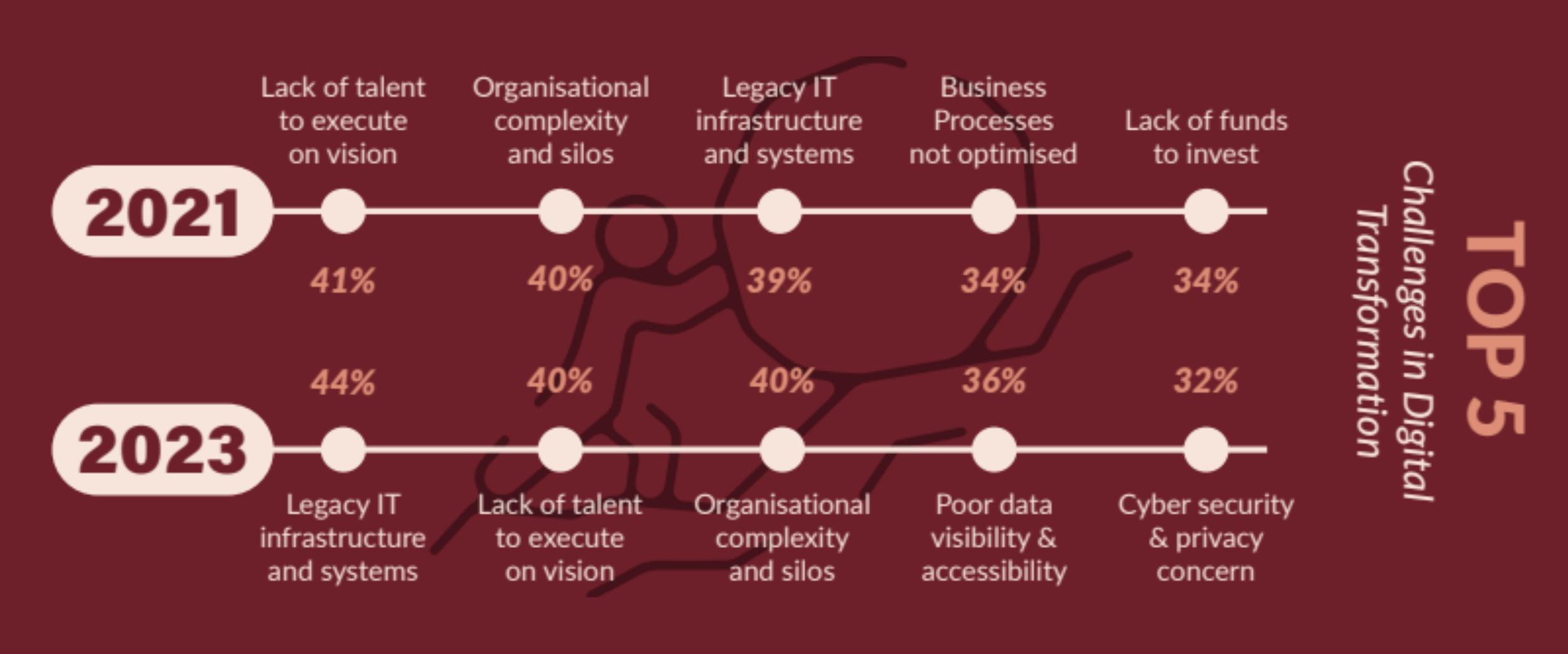
In 2023, Cybersecurity and Privacy Concerns has gained increased prominence as one of the Top 5 Challenges to Digital Transformation for Southeast Asian Enterprises. Whilst Legacy IT takes top spot highlighting vulnerabilities of systems to cyber incidents.
In a 2024 study conducted by AIBP, it reveals a significant discrepancy between what organisations are currently spending on cybersecurity and what they believe they should be spending.
These figures indicate that while a significant portion of organisations are currently spending less than they believe is necessary, there is a clear intention among many to increase their cybersecurity investments. For instance, among Malaysia respondents, only 9% of organisations are spending more than 20% of their IT budget on cybersecurity, whereas 52% believe they should be allocating this amount.
Adequate budget allocation is crucial for implementing comprehensive cybersecurity measures, from acquiring advanced security technologies to ensuring continuous training and awareness programs for employees.
Current vs. Ideal Cybersecurity Spending
AIBP Networking: Cyber Resilience
Together with YBhg. Dato' Ts. Dr. Haji Amirudin Bin Abdul Wahab, Chief Executive Officer of CyberSecurity Malaysia, we are hosting an exclusive industry networking, covering 3 key topics around the role of technology in our business & along the ecosystem to:
Mitigate Risks through Proactive Cyber Risk Management and Resilience Strategies
Explore Governance Frameworks for Cloud and Data in Emerging Technologies
Leveraging Technologies to Strengthen Cyber Resilience in a Dynamic Threat Landscape
Agenda
2:30 - 3:00 PM | Registration & Networking
3:00 - 3:05 PM | Introduction by AIBP
3:05 - 3:15 PM | Welcome Remarks by YBhg. Dato’ Ts. Dr Haji Amirudin Bin Abdul Wahab, Chief Executive Officer, CyberSecurity Malaysia
3:15 - 4:00 PM | Tech Update #1 - From Reactive to Predictive: AI's Role in Transforming GRC Strategies
4:05 - 4:50 PM | Tech Update #2 - Future-Proofing Compliance: Cloud-Native GRC for Evolving Regulatory Landscapes
4:55 - 5:40 PM | Tech Update #3 - Navigating Complexity: Piecing Together an Integrated Risk Management Strategy
CSM x AIBP Tech Update - Join us on 3 Dec
The Malaysia Cyber Security Act 2024 integrates risk management principles aligned with Governance, Risk, and Compliance (GRC) frameworks, with a focus on National Critical Information Infrastructure (NCII) entities. This legislation mandates NCII organizations to implement regular risk assessments and audits, which form the cornerstone of effective GRC practices. Explore the forefront of GRC innovation in this session, where participants will uncover:
The transformative impact of AI on GRC strategies, shifting from reactive measures to proactive, predictive methodologies
The role of cloud-native solutions in future-proofing compliance amidst a rapidly evolving regulatory environment
Advanced techniques for tackling the intricacies of contemporary risk management through holistic, integrated approaches
This session is designed to empower professionals with cutting-edge knowledge, enabling them to harness emerging technologies and methodologies. Attendees will gain the expertise needed to position their organisations at the vanguard of compliance and risk management in the digital age, aligning with the forward-thinking principles embodied in Malaysia's Cyber Security Act 2024.
Register your Interest
Interested in getting involved in our upcoming activities?
Fill up the form if you would like to:
Attend
Join as a Speaker; or
Sponsor
Our representatives will be in touch.
Past Activities
Cybersecurity Stakeholders We’ve Worked With